What is Cryptojacking and How Windows Users Can Be Protected
As digital technology and internet connectivity advance, so do the threats to our online security. Among these emerging dangers, cryptojacking has become a pervasive risk for internet users.
We will examine cryptojacking, its causes, examples, and how to protect yourself and your Windows PC from this evolving, intrusive threat. By understanding how cryptojacking works and implementing adequate safeguards, users can better defend their systems and control their computing resources.
What is Cryptojacking?

Cryptojacking is a malicious practice in which cybercriminals hijack a victim’s computing resources through malware to mine cryptocurrency without their knowledge or consent. This covert operation can affect various devices, including personal computers, smartphones, and servers.
Cryptojacking has become popular among cybercriminals due to rising cryptocurrency values. It differs from ransomware in that it doesn’t demand immediate payment. Instead, cryptojacking works quietly in the background, potentially allowing attackers to earn money over extended periods.
Signs of Cryptojacking Malware Infection
Detecting cryptojacking can be challenging due to its subtle nature. However, Windows users should be aware of these common indicators:
Performance Issues
- Unexplained slowdowns in system performance
- Unusual spikes in CPU usage
- Overheating of devices, even during minimal activity
Power Consumption
- Increased electricity bills without apparent reason
- Batteries draining faster than usual on laptops
Browser Behavior
- Web pages take longer to load
- Sudden crashes or unresponsiveness in browsers
How Does Cryptojacking Work?

Cryptojacking typically occurs through two main methods:
Browser-Based Cryptojacking: Attackers inject malicious JavaScript code into websites. When users visit these compromised sites, the script runs in the background, utilizing the visitor’s CPU to mine cryptocurrency.
File-Based Cryptojacking: Cybercriminals deploy malware through phishing emails or infected downloads. Once installed, this malware runs continuously, mining cryptocurrency in the background.
5 Ways on How to Protect Yourself Against Cryptojacking
Keep Your System Updated
Keeping your system updated is crucial in defending against cryptojacking. Regular updates patch known vulnerabilities that cybercriminals might exploit. This simple yet effective practice can significantly reduce your risk of falling victim to cryptojacking attempts.
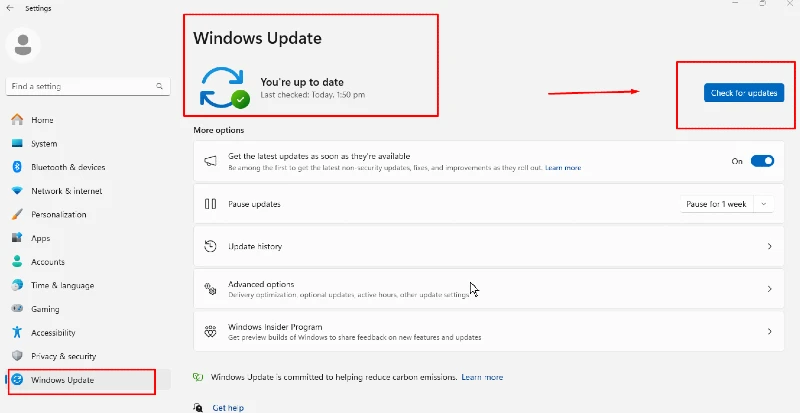
- Click Start > Settings > Update & Security
- Select “Windows Update”
- Click “Check for updates
- If available, click “Download and install.”
- Restart when prompted
Use Reputable Antivirus Software with Malware Defense
A robust antivirus program is a vital line of defense against cryptojacking malware. It can detect and prevent cryptojacking attempts before they infiltrate your system. Choosing a reputable antivirus solution with real-time protection is essential for maintaining your computer’s security.
While Windows has built-in security features, consider investing in an extensive third-party security solution for enhanced protection. For example, Fortect is a premium service that offers automatic malware scanning, including detecting cryptojacking threats. It identifies and isolates potential threats, notifies you of any issues, cleans your system, and optimizes performance.
Such all-in-one solutions can provide your Windows PC security and peace of mind.
Download and install Fortect now.
Install Browser Extensions
Browser extensions are specifically designed to block cryptojacking scripts that can provide additional protection. These tools prevent malicious mining scripts from running in your browser, effectively stopping browser-based cryptojacking attempts. Integrate popular web browser extensions like minerBlock, No Coin, and Anti Miner to create a protective barrier against cryptojacking across various websites.
These lightweight yet powerful additions to your browser’s functionality can significantly reduce the risk of being victim to stealthy mining operations while surfing the web.
Practice Safe Browsing

Safe browsing habits are fundamental in preventing various cyber threats, including cryptojacking. Being cautious about the links you click and the files you download can significantly reduce your exposure to potential cryptojacking attempts.
- Be cautious of unknown sender emails.
- Avoid clicking suspicious links.
- Download only from official websites.
- Look for HTTPS (padlock icon) in the address bar
- Close suspicious pop-ups
- Use Windows SmartScreen
Monitor System Performance
Regular monitoring of your system’s performance can help you detect cryptojacking early. Unusual spikes in CPU usage or unexpected slowdowns can indicate cryptojacking activity. You can quickly catch and address potential threats by staying vigilant and investigating anomalies.
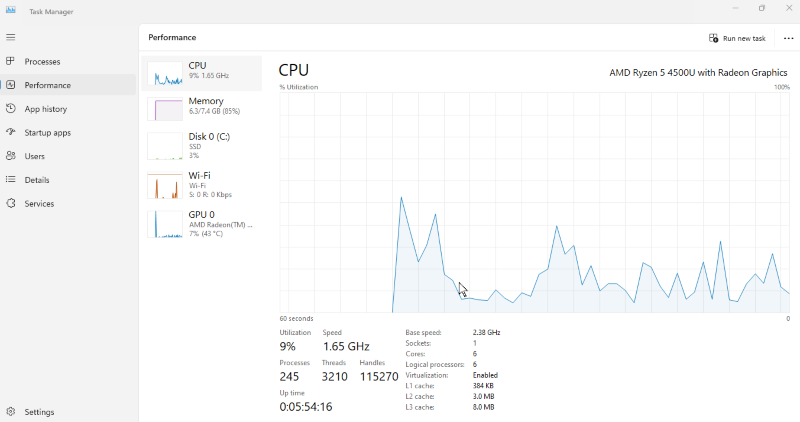
- Right-click taskbar > Task Manager
- Click “More details” if needed
- Go to the “Performance” tab
- Monitor CPU, Memory, and GPU usage
- Check the “Processes” tab for resource-heavy apps
- Research suspicious processes online
Conclusion
Cryptojacking poses a significant threat to Windows users, potentially compromising system performance and security. By understanding the signs of infection and implementing robust protection measures, users can safeguard their devices against this insidious cybercrime. Stay vigilant, update your system, and prioritize cybersecurity to ensure a safe computing experience.




