Spyware: What It Is and How Windows Users Can Be Protected
Safeguarding personal information while using the internet is more crucial than ever.
We will examine what spyware is, explain it, and offer essential tips for Windows users to protect themselves from these stealthy threats.
What is Spyware?
Spyware is a malicious program installed on your computer or mobile device without your consent or idea. It can access your personal information, banking details, and other sensitive information meant only for you and will exploit it or even relay it to other parties. This is a hazardous situation that every computer user should be aware of so they can take precautions or protect themselves.
What Does Spyware Do, and What are the Types of Spyware

Spyware works on its own after being programmed to infiltrate. Primary targets include financial sector employees, vulnerable individuals, and retirees. Governments deploy spyware against foreign nations and high-profile figures, potentially influencing global affairs.
Below are the known things that spyware can do:
- Monitors your activity without consent
- Records keystrokes to capture passwords and sensitive data
- Track your browsing history and online behavior
- Accesses your files and documents
- Captures of screenshots or webcam images
- Logs communication data (emails, messages, calls)
- Gathers system information and installed software details
- Transmits collected data to unauthorized parties
- May allow remote control of the infected device
- Often hides its presence to avoid detection
These are the most common ones that you should be aware of. You should look at the types of spyware to understand its hideous community of deceit.
Types of Spyware
Adware: Displays unwanted ads and tracks browsing habits. Often bundled with free software, it can slow devices and compromise privacy.
Keyloggers: Record keystrokes to capture sensitive data like passwords. It can be software or hardware-based, posing a severe threat to personal security.
Trojans: Malicious programs disguised as legitimate software. Create backdoors for unauthorized access and can install other malware.
Tracking Cookies: Small files that monitor online behavior across multiple sites. Create user profiles and persist after browsing sessions, raising privacy concerns.
Mobile Spyware: Targets smartphones, accessing location data, messages, and calls. Often installed through malicious apps, it’s highly invasive due to the personal nature of mobile devices.
Infostealers: Focus on harvesting specific data types like financial information or intellectual property. Spread through phishing attacks and can cause significant economic or proprietary damage.
How to Protect Yourself from This Threat
Keep Windows up to date
Maintain current security patches on all software. Cybercriminals exploit vulnerabilities in outdated operating systems and applications to install malware. Prompt application of updates is crucial, as they often contain fixes for known security flaws.
Breadcrumbs Navigation
Start >Settings > Windows Update ( lower left for Windows 10 ) > Make sure that Windows is up to date. If not, click Check for Updates or Install Updates as shown above.

It’s paramount to keep your Windows up to date to avoid unnecessary threats. You may check our article on Should You Always Update Windows to learn more about the pros and cons of Windows updates.
Avoid Email Links and Attachments from Unknown Sources
Exercise caution with email links and attachments from unfamiliar senders, as they’re common vectors for spyware and other malware. Verify the sender’s identity before interacting with any email content, and use built-in email security features to scan attachments for potential threats. Don’t open or click on suspicious links or attachments.
It’s best practice to delete questionable emails without opening them.
Enable or Download a Pop-up blocker
Pop-up blockers are essential for enhancing online security and browsing experience. They prevent unwanted windows from appearing, which often contain ads, malware, or phishing attempts.
Here’s how to enable or download a pop-up blocker for your browser:
Check your browser settings first, as most modern browsers have built-in pop-up blockers.

For Chrome, go to Settings > Privacy and Security> Site Settings > Scroll down, look for Pop-ups and redirects > Don’t allow sites to send pop-ups or use redirects

In Firefox, click the menu button, select Options, then Privacy & Security. Under Permissions, check “Block pop-up windows.
If you need additional protection, consider downloading a dedicated pop-up blocker extension from your browser’s web store.
Choose a reputable extension with high user ratings and recent updates.
After installation, configure the extension’s settings according to your preferences.
Invest in Third-party Antivirus and Malware Defense Software
Investing in third-party malware defense software protects against various cyber threats, including spyware. Cybersecurity threats like spyware, malware, and viruses remain persistent risks for any device connected to the Internet.
Consider Fortect, an all-in-one PC solution with real-time malware defense. It scans your system for various threats, eliminates them, and efficiently restores your PC to optimal performance significantly faster than manual methods.
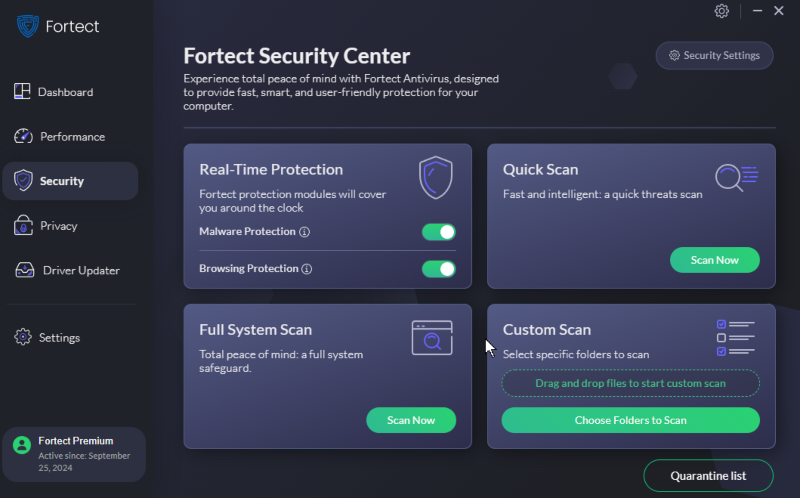
Download and install Fortect now to avoid any dangers, such as spyware and other cybersecurity threats on the internet.
Limit Applications to a Pre-approved Allowlist
Implementing a pre-approved allowlist for applications significantly enhances system security by restricting execution to trusted software only.
Here’s how to set it up:
- Create a comprehensive list of essential applications for your system.
- Use built-in operating system features like Windows AppLocker
- For Windows, access the Local Security Policy and configure Application Control Policies.
- Implement third-party application control software for more granular management.
- Regularly review and update your allowlist to accommodate new, necessary applications.
- Train users on the policy and establish a transparent process for requesting new app approvals.
- Monitor system logs to detect and investigate any attempts to run unauthorized software.
Conclusion
Spyware remains a significant threat in our increasingly connected digital world. Vigilance, regular software updates, and robust security measures are crucial to protect personal and sensitive information. While no solution guarantees complete immunity, combining safe browsing habits, strong passwords, and reliable anti-malware tools significantly reduces the risk of spyware infections.
Stay informed about emerging threats and prioritize digital security to safeguard your online presence and data integrity.




