How to Detect Network Sniffing on Your Windows Device
Network sniffing can silently compromise your digital security. It’s the act of intercepting and logging traffic passing over a network, which can lead to password theft, data leaks, or worse—full device compromise. If you’re using Windows 10 or 11, it’s crucial to know how to detect sniffing attempts early and take proper action.
We will help you detect network sniffing on your Windows device and show you how to secure your system against potential eavesdroppers.
What Is Network Sniffing?
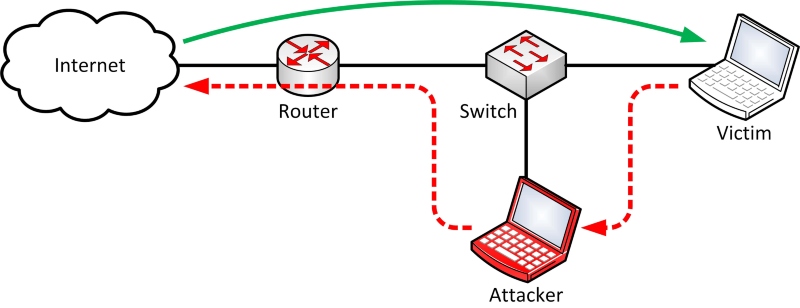
Network sniffing refers to monitoring data packets transmitted over a network. While legitimate in some IT diagnostics scenarios, it’s often used by cybercriminals to capture sensitive information like login credentials, emails, and credit card numbers.
There are two main types of sniffing:
- Passive Sniffing: Monitors unencrypted traffic without interfering.
- Active Sniffing: This involves injecting traffic into a network to gain more access or redirect communications.
Common Signs of Network Sniffing
Identifying a sniffing attempt isn’t always straightforward, but here are signs that should raise red flags:
- Slow or laggy internet connections
- Unexpected SSL/TLS certificate warnings
- Suspicious processes using ports like 80, 443, or 21
- Unusual traffic in network monitoring tools
- Devices unexpectedly added to your network
How to Detect Network Sniffing on Windows
1. Use the Command Prompt to Spot Promiscuous Mode
A Windows machine in promiscuous mode may be capturing traffic not intended for it.
Steps:
- Press Windows + R, type cmd, and press Enter.
- Type netstat -an and press Enter.
- Look for foreign IP addresses or strange port numbers.
Alternatively, use this command:
- Get-NetAdapter | Select Name, MacAddress, Status, PromiscuousMode
If PromiscuousMode is enabled, you should investigate further.
2. Monitor Network Traffic with Windows Resource Monitor
You can track active connections using the built-in Resource Monitor.
Steps:
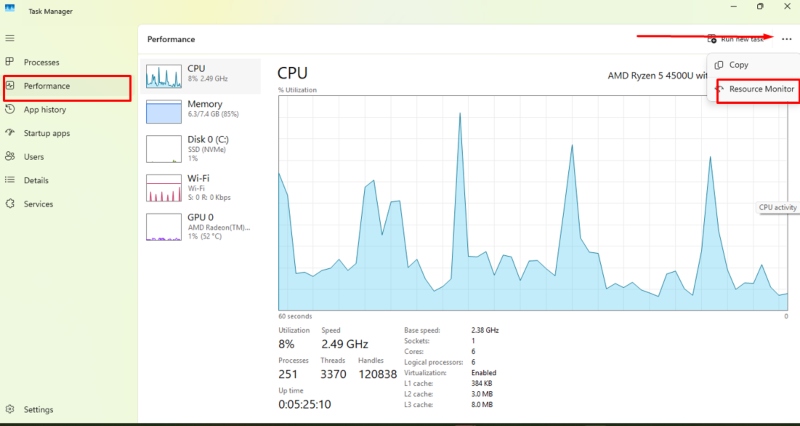
- Press Ctrl + Shift + Esc to open Task Manager.
- Go to the Performance tab and click Open Resource Monitor.
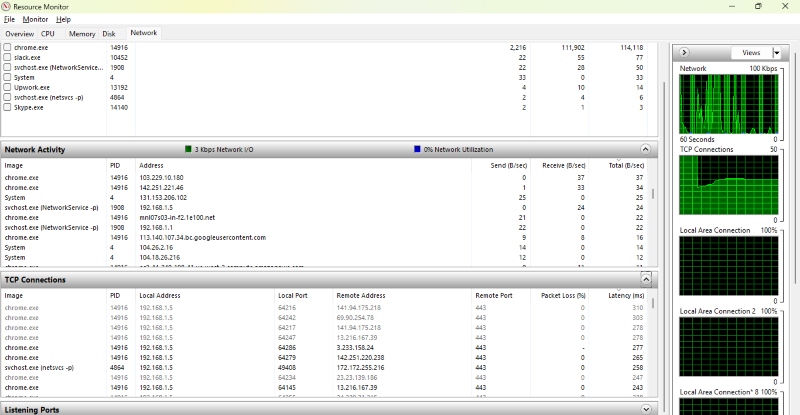
- Select the Network tab.
- Check “Processes with Network Activity” and “TCP Connections.”
Look out for processes that shouldn’t be accessing the network or external IPs that look suspicious.
3. Install a Packet Sniffer to Detect Other Sniffers
It may sound ironic, but using a tool like Wireshark can help you identify sniffing activities or misconfigured traffic.
What to look for in Wireshark:
- ARP Spoofing attempts
- DNS poisoning
- Duplicate IPs
- Unusual or unauthorized protocols
Set filters like http, ftp, or telnet to check for unencrypted traffic leaks.
4. Update Windows to Patch Security Holes
Outdated systems are vulnerable to exploits, including sniffing-based attacks.
Steps to Update Windows 10/11:
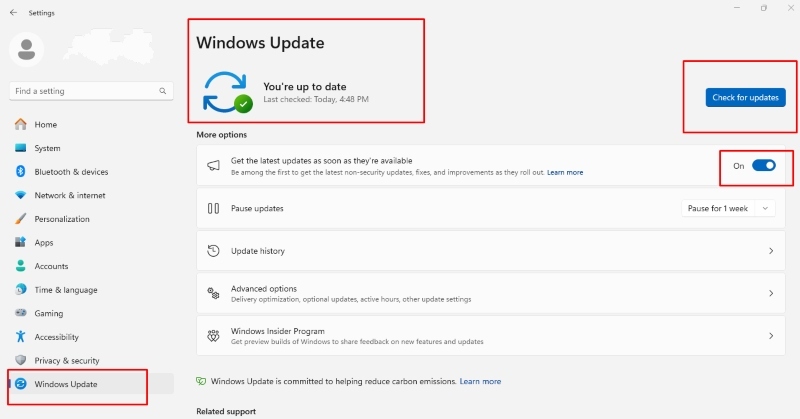
- Click Start → Settings.
- Select Update & Security.
- Click Windows Update from the sidebar.
- Click Check for updates and install any available updates.
Staying updated helps prevent attackers from exploiting known vulnerabilities.
5. Restrict User Access to Reduce Risks
Limiting who can connect to or administer your PC reduces the chances of internal sniffing.
Steps to Restrict Users:
- Open Settings → Accounts → Family & other users.
- Under “Other users,” click on the account you want to restrict.
- Choose Change account type and select Standard User instead of Administrator.
- Remove unnecessary accounts entirely if not needed.
6. Run a Network Scan with Fortect (Recommended)
If you suspect someone may be sniffing your connection or your PC may have hidden malware collecting data silently, run a malware scan.
Fortect is an all-in-one PC repair tool that offers real-time malware protection. It automatically scans your Windows system for known and unknown malware—especially sniffing-related tools that could be running quietly in the background. This can help detect and stop malicious programs designed to intercept your data before they cause serious damage.
Use Fortect to perform a deep system scan and catch stealthy sniffing malware before it gets dangerous.
Download Fortect today.
Extra Tips to Prevent Network Sniffing
Use Encrypted Connections
Using HTTPS encrypts the data between your browser and a website, making it unreadable to packet sniffers. Even if intercepted, the information appears as scrambled code. Sites like online banks and email services use HTTPS to keep your data secure.
Use a VPN
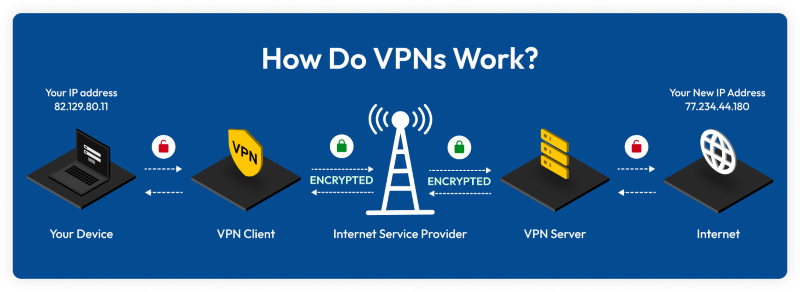
A VPN encrypts your entire internet traffic, making it useless to sniffers. Choose a reputable provider with AES-256 encryption.
Secure Your Wi-Fi
- Use WPA3 if available, or at least WPA2
- Change the default router login credentials
- Hide your SSID if possible
- Enable MAC address filtering
Final Thoughts
Network sniffing is an invisible threat—but not undetectable. With the right tools and techniques, you can spot unusual traffic, detect compromised systems, and lock down your Windows device. Regular updates, smart user restrictions, and strong monitoring habits will go a long way in protecting your data. If you suspect that sniffing malware is already lurking in your system, running a deep malware scan with Fortect is a smart and fast way to regain control.




