How to Prevent Hyper-V Exploits in Windows 11
Hyper-V is a powerful virtualization tool integrated into Windows 11, enabling users to run multiple operating systems on a single device. However, attackers can exploit vulnerabilities within Hyper-V to compromise system security. Threats like the Office SharePoint flaw and CVE-2024-38112 have raised concerns about potential exploitation routes.
Fortect will guide you in safeguarding your Windows 11 system against Hyper-V exploits using adequate security measures.
Understanding Hyper-V Vulnerabilities
Hyper-V vulnerabilities pose significant security risks as they can allow attackers to gain unauthorized access, execute malicious code, or disrupt system operations. Exploits such as CVE-2024-38112 highlight the importance of timely updates and proper system configurations. Addressing these vulnerabilities is crucial to maintaining system integrity and preventing cyberattacks.
Hyper-V Exploits in Windows 11 Prevention
Keep Windows and Hyper-V Updated
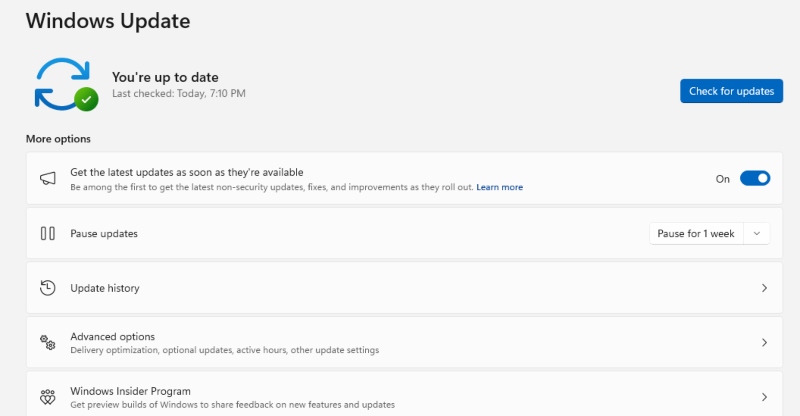
In addition to installing the latest Windows 11 security update, also update Hyper-V is essential to protect against known vulnerabilities.
Microsoft frequently releases security patches to address newly discovered vulnerabilities, including flaws in Hyper-V. Updates often resolve issues like the Office SharePoint flaw and vulnerabilities identified under CVE listings.
- Press Windows + I to open Settings.
- Click on Windows Update.
- Select Check for updates and install any available updates.
- Restart your system to apply updates.
Enable Secure Boot and TPM
Secure Boot and Trusted Platform Module (TPM) add layers of security to your system, making it harder for attackers to exploit Hyper-V.
Secure Boot prevents unauthorized firmware from loading during startup, while TPM securely stores cryptographic keys. These features work together to reduce the risk of Hyper-V-based attacks.
- Restart your PC and enter the BIOS/UEFI settings.
- Locate Secure Boot and TPM options.
- Enable both settings and save changes.
- Restart the system.
Configure Hyper-V Settings for Security
Properly configuring Hyper-V reduces attack surfaces and strengthens your system’s defenses.
Key Security Configurations
Misconfigured Hyper-V settings can expose your system to risks. Implementing network isolation and limiting resource sharing can mitigate threats like CVE-2024-38112.
- Open Hyper-V Manager from the Start menu.
- Right-click on the virtual machine and select Settings.
- Configure Network Adapter to use isolated virtual switches.
- Disable unnecessary integration services.
Use Antivirus and Antimalware Solutions
A robust security solution can detect and block attempts to exploit Hyper-V vulnerabilities.
Advanced malware can target system components, including Hyper-V. Comprehensive security software can detect exploit attempts and prevent unauthorized access.
Recommended Security Practices
- Install reputable antivirus software.
- Enable real-time protection and automatic updates.
- Perform regular system scans.
Enhance Your Protection with Fortect
Fortect is an advanced antivirus solution with real-time malware protection for today’s sophisticated cyber threats. It thoroughly scans your Windows PC for malware, vulnerabilities, corrupted files, and system issues, automatically fixing them in minutes while optimizing your PC for peak performance.
Strengthen your security with Fortect and stay ahead of potential exploits.
Download and install Fortect now.
Monitor and Manage Virtual Machines
Regular virtual machine (VM) monitoring can help detect suspicious activities linked to potential exploits.
Monitoring VMs allows early detection of unusual behavior, reducing the risk of exploitation. This practice is essential for identifying attacks exploiting vulnerabilities like CVE-2024-38112.
- Open Hyper-V Manager.
- Use Performance Monitor to track resource usage.
- Review event logs for irregular activities.
Disable Unused Hyper-V Features
Reducing unnecessary features limits the system’s exposure to threats.
Benefits of Feature Reduction
Unused Hyper-V components can serve as entry points for attackers. Disabling these reduces the potential attack surface.
- Press Windows + R, type optionalfeatures.exe, and press Enter.
- Uncheck unused Hyper-V components.
- Click OK and restart your PC.
Conclusion
Protecting your Windows 11 system from Hyper-V exploits requires proactive security practices, from regular updates and secure configurations to robust antivirus solutions. Implementing these strategies minimizes risks related to vulnerabilities like CVE-2024-38112 and the Office SharePoint flaw, ensuring a secure virtualization environment.




