How to Prevent Keylogger Attacks on Your Windows PC
Keyloggers significantly threaten your privacy and security by secretly recording your keystrokes to capture sensitive information like passwords, credit card numbers, and personal messages.
We will help you understand what keyloggers are, identify signs of their presence, and take proactive measures to protect your Windows PC from such attacks.
What Is a Keylogger and How Does It Work?
A keylogger is a type of malware designed to record every keystroke you make on your keyboard. The attacker can then use this information to gain unauthorized access to your accounts and personal data. Keyloggers can be installed through malicious software downloads, email attachments, or even physical access to your device.
Signs That There’s a Keylogger on Your Windows Device

Identifying a keylogger on your Windows device can be challenging, but there are some common signs to watch for:
- Prolonged performance
- Frequent crashes or freezes
- Unknown applications running in the background
- Unexpected pop-ups or ads
- Increase in network activity when the computer is idle
5 Ways To Protect Your System from Keylogger Attacks
Keep Windows Updated
Regularly updating Windows ensures you have the latest security patches and fixes for vulnerabilities that attackers might exploit.
Steps:
- Open Settings from the Start menu.
- Go to Update & Security.
- Click on Windows Update.
- Select Check for updates and install any available updates.
Install a Password Manager
A password manager generates and stores complex passwords, reducing the risk of password theft through keyloggers.
Steps:
- Choose a reputable password manager (e.g., LastPass, 1Password).
- Download and install the application.
- Follow the setup instructions to create an account and store your passwords.
Set Up a Firewall
A firewall monitors incoming and outgoing network traffic and blocks unauthorized access, adding an extra layer of security against keyloggers.
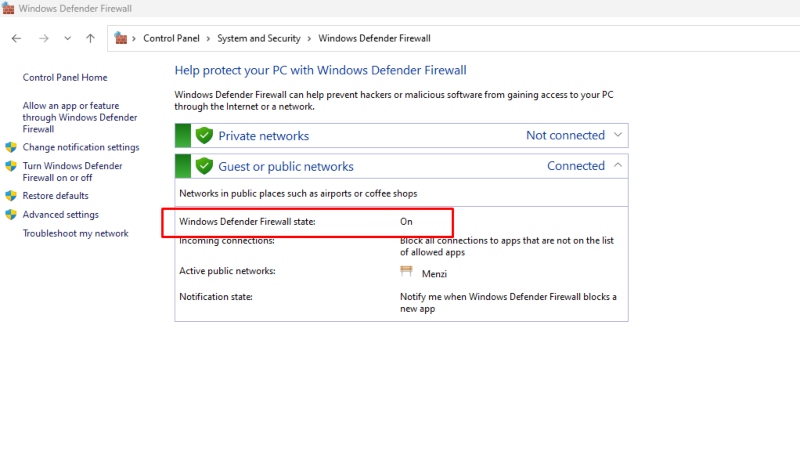
Steps:
- Open the Control Panel and go to System and Security.
- Click on Windows Defender Firewall.
- Select Turn Windows Defender Firewall on.
- Ensure the firewall is turned on for both private and public networks.
Get Antivirus Software with Malware Defense
It’s good practice to set up your firewall via Windows Defender. A firewall is an excellent practice to add an extra layer of protection when attackers become more advanced and sophisticated. Antivirus software detects and removes keyloggers and other malware, ensuring your system remains secure.
Consider investing in Fortect with Malware Defense. Fortect Premium automatically scans all installed software on your Windows PC, detects malware and other threats like keyloggers, and provides real-time updates. It then fixes the problems and optimizes your Windows PC’s performance to its highest peak.
Download and install Fortect now.
Routinely Change Your Passwords
Regularly changing your passwords minimizes the risk of keylogger attacks by reducing the time an attacker can access your accounts.
Steps:
- Create a schedule to change passwords every 3-6 months.
- Use a password manager to generate strong, unique passwords.
- Update your passwords across all accounts, especially for sensitive services like banking and email.
Why Do Hackers Use Keyloggers?
Hackers use keyloggers primarily to steal sensitive information such as login credentials, financial data, and personal communications. This information can be used for identity theft, financial fraud, or sold on the dark web. Keyloggers are insidious because they operate silently, often going undetected for extended periods, allowing attackers to gather extensive data over time.
Conclusion
Protecting your Windows PC from keylogger attacks requires a combination of proactive measures and vigilant practices. You can significantly reduce the risk of keylogger infections by keeping your system updated, using strong passwords, setting up firewalls, and installing robust antivirus software.
Monitoring your device regularly for signs of malware and staying informed about the latest security threats will also help you maintain a secure computing environment.




