How to Prevent LSASS Credential Dumping Attacks in Windows
Credential security is a top priority for Windows users, especially when protecting sensitive login information. One of the most targeted components in Windows systems is the Local Security Authority Subsystem Service (LSASS), a process responsible for enforcing security policies and managing user authentication.
Cybercriminals often exploit LSASS through credential dumping attacks or credential theft to extract sensitive information like usernames and passwords. This Fortect guide explains how LSASS credential dumping works and provides actionable steps to prevent these attacks on Windows 10 and 11 systems.
LSASS Memory Dump Files
LSASS memory dump files are snapshots of the LSASS process stored on a system. These files can contain sensitive information, such as plaintext credentials, NTLM hashes, and Kerberos tickets. Attackers leverage these dumps to extract login credentials using tools like Mimikatz.
Preventing unauthorized access to LSASS memory is crucial for maintaining the security of Windows systems and protecting against data breaches.
How to Prevent LSASS Credential Dumping Attacks
Enable Windows Defender Credential Guard
Windows Defender Credential Guard is a security feature that isolates and protects credentials using virtualization-based security. It ensures that secrets stored in LSASS are not accessible by malware or unauthorized users. By enabling Credential Guard, Windows systems can effectively block tools designed for credential dumping.
Steps to Enable Windows Defender Credential Guard on Windows 10/11
- Enable Virtualization in BIOS/UEFI:
- Restart your PC and enter the BIOS/UEFI settings (commonly by pressing Del or F2 during startup).
- Locate and enable Intel VT-x or AMD-V and Virtualization-based Security (VBS) options.
- Save changes and exit.
- Turn On Windows Features:
- Press Win + R, type optionalfeatures, and press Enter.
- Check Isolated User Mode and Hyper-V.
- Click OK and restart your PC if prompted.
- Enable Credential Guard via Group Policy:
- Press Win + R, type gpedit.msc, and press Enter.
- Navigate to Computer Configuration > Administrative Templates > System > Device Guard.
- Double-click Turn On Virtualization Based Security.
- Select Enabled, and under Credential Guard Configuration, choose Enabled with UEFI lock or Enabled without a lock.
- Click OK and restart the PC.
- Verify Credential Guard Status:
- Open Command Prompt as an administrator.
- Type systeminfo and press Enter.
- Look for Device Guard Properties to confirm that Credential Guard is running.
Keep Windows and Security Software Updated
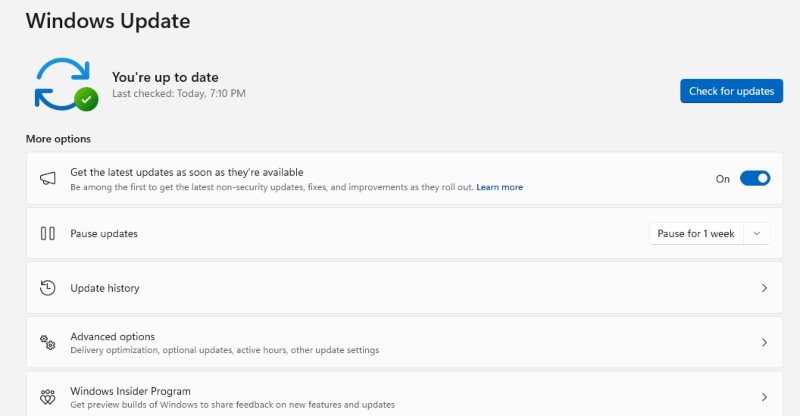
Regular updates patch security vulnerabilities that attackers exploit. Microsoft frequently releases security patches that address potential exploits targeting LSASS. Keeping Windows OS and security software up-to-date ensures protection against known vulnerabilities and reduces the risk of credential dumping.
Steps to Keep Windows and Security Software Updated
- Enable Automatic Windows Updates:
- Press Win + I to open Settings.
- Go to Update & Security > Windows Update.
- Click Advanced options and enable Automatically download updates.
- Manually Check for Windows Updates:
- Press Win + I to open Settings.
- Navigate to Update & Security > Windows Update.
- Click Check for updates and install any available updates.
- Update Windows Defender and Security Software:
- Open Windows Security by pressing Win + S and typing Windows Security.
- Go to Virus & Threat Protection.
- Click Check for updates under Virus & Threat Protection updates.
- Install Driver and Firmware Updates:
- Open Device Manager by pressing Win + X and selecting Device Manager.
- Right-click on devices and select Update driver.
- Visit your hardware manufacturer’s website for firmware updates.
Restrict LSASS Access Permissions
To protect LSASS (Local Security Authority Subsystem Service) from unauthorized access, you can limit who can interact with it. In Windows 10 and 11, you can adjust User Account Control (UAC) settings.
Here’s how:
- Open Control Panel > User Accounts > Change User Account Control settings.
- Set it to Always Notify to ensure your system warns you before making changes.
- Additionally, you can use Local Group Policy (for Pro and Enterprise versions) to restrict access further:
- Press Windows + R, type gpedit.msc, and hit Enter.
- Navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment.
- Adjust policies that control who can log in as a user or administrator.
Disable LSASS Memory Dumping
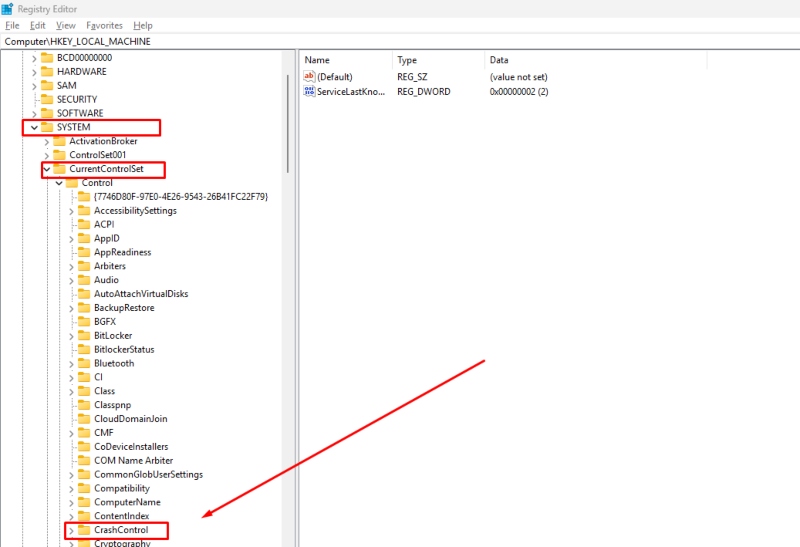
Turning off LSASS memory dumping prevents the creation of dump files that attackers could use to extract credentials. Configuring group policies or registry settings to block LSASS dumping adds a layer of protection against credential theft.
- Press Windows + R, type regedit, and hit Enter.
- Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\CrashControl.
- Find the value CrashDumpEnabled and set it to 0.
This will stop your system from creating memory dumps that could be exploited.
Use Endpoint Detection and Response (EDR) Solutions
EDR tools help detect malicious activity in real-time, such as when someone tries to access LSASS memory. Many third-party security tools like Windows Defender Antivirus have built-in protection:
Enable Real-time protection by going to Settings > Update & Security > Windows Security > Virus & Threat Protection.
Use additional third-party EDR software, such as Fortect or Kaspersky, for more advanced protection.
Apply the Principle of Least Privilege (PoLP)
Granting users only the minimum necessary permissions reduces potential attack surfaces. Restricting administrative access and removing unnecessary privileges can prevent attackers from gaining the level of access required to interact with LSASS.
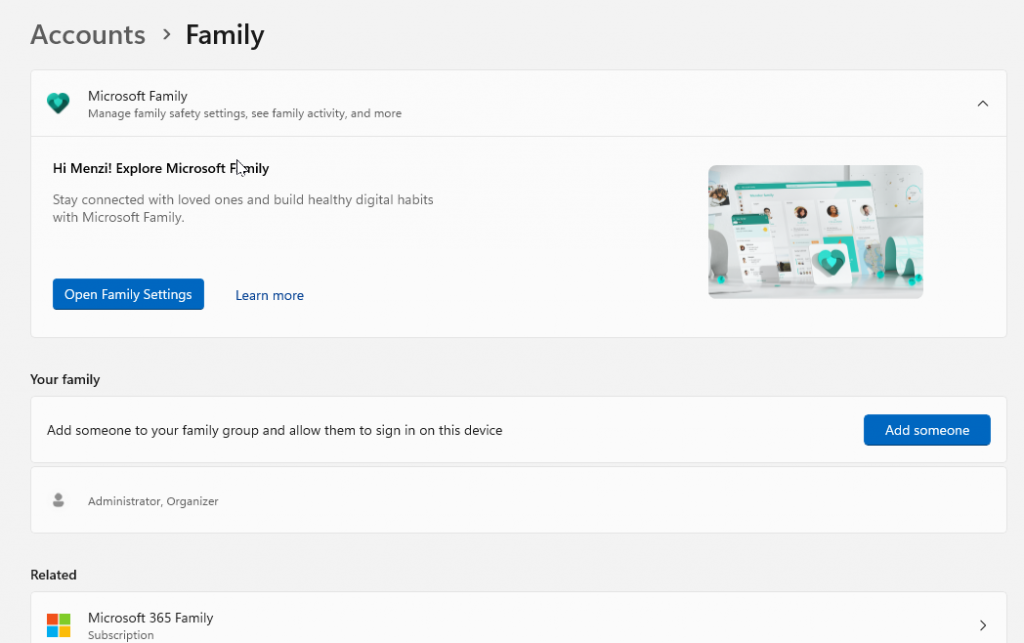
Limit user permissions to only what’s necessary. This minimizes the chances of attackers gaining high-level access:
Go to Settings > Accounts > Family & other users to manage who has admin access.
If someone doesn’t need administrator rights, set them to Standard User instead.
Regularly review who has admin privileges and remove unnecessary access.
Monitor System Logs and Security Events
Monitoring system logs can help detect suspicious activities related to LSASS access. Security Information and Event Management (SIEM) tools can also track unusual behavior and alert administrators of potential attacks. Early detection is key to preventing credential theft.
Steps to Monitor System Logs and Security Events
- Use Event Viewer to Monitor Logs:
- Press Win + X and select Event Viewer.
- Navigate to Windows Logs > Security to review security-related events.
- Look for suspicious activities, such as failed logins or unexpected account changes.
- Enable Advanced Auditing Policies:
- Press Win + R, type gpedit.msc, and press Enter.
- Go to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration.
- Enable auditing for Logon/Logoff, Account Logon Events, and Process Creation.
- Set Up Security Alerts in Windows Security:
- Open Windows Security by pressing Win + S and searching for Windows Security.
- Go to Virus & Threat Protection> Manage settings.
- Enable Notifications for detected threats and actions taken.
- Implement SIEM Tools for Advanced Monitoring:
- Deploy SIEM solutions like Microsoft Sentinel or Splunk for comprehensive log analysis.
- Configure alerts for suspicious LSASS-related activities.
- Regularly Review Audit Logs:
- Schedule routine log reviews to detect anomalies.
- Archive logs securely for future analysis and compliance purposes.
Protect Your PC with Fortect
Fortect is an all-in-one PC repair solution that offers real-time malware protection, preventing cybercriminals from exploiting LSASS memory dumps. It automatically scans your Windows PC for potential threats, delivers real-time notifications, and repairs system vulnerabilities in minutes while optimizing overall performance.
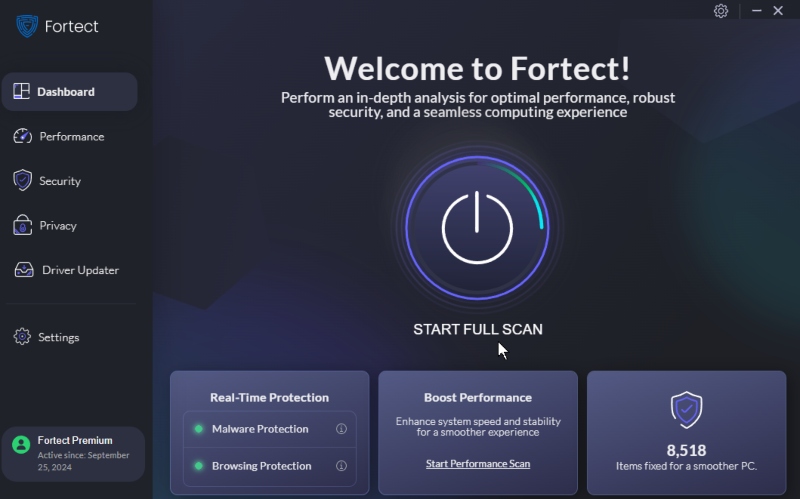
Key Benefits of Using Fortect
- Real-Time Malware Protection: Detects and blocks malware that targets LSASS memory dumps.
- Automatic Threat Detection: Continuously scans your system for vulnerabilities and notifies you of any detected issues.
- System Repair and Optimization: Quickly fixes system errors and optimizes PC performance for smooth operation.
Integrating Fortect into your security strategy can enhance your defense against LSASS credential dumping attacks and maintain a secure Windows environment.
Download and install Fortect now.
Final Thoughts
LSASS credential dumping attacks seriously threaten Windows systems, making proactive security measures essential. Users can significantly reduce the risk of credential theft by enabling Windows Defender Credential Guard, updating software, restricting access, and implementing advanced security solutions.
Staying vigilant and applying these preventative strategies will help protect sensitive credentials and maintain system integrity.




