Remote Desktop Protocol Risks and How to Protect Your Windows PC
The Remote Desktop Protocol (RDP) allows users to connect to another computer over a network connection. While it offers convenience for remote access, it also poses significant risks that can compromise your Windows PC.
Understanding Remote Desktop Protocol (RDP)
RDP is a proprietary protocol developed by Microsoft that enables users to control other Windows computers remotely. It is widely used in corporate environments for remote administration and technical support. However, the features that make RDP helpful expose systems to various vulnerabilities.
Key Features of RDP
RDP offers features such as file transfer, printer sharing, and audio redirection, enhancing the remote user experience. Its encrypted communication provides a level of security, but the complexity of these features can create potential entry points for malicious actors. Understanding these features is crucial for recognizing the associated risks.
Risks of Remote Desktop Protocol (RDP)
While convenient, RDP can expose your Windows PC to several risks. Cybercriminals actively exploit RDP vulnerabilities to gain unauthorized access, steal sensitive data, and launch attacks.
- Brute Force Attacks: One of RDP’s primary risks is its susceptibility to brute-force attacks. Attackers can use automated tools to guess login credentials by rapidly trying multiple combinations. If strong passwords are not enforced, this can lead to unauthorized access to your system.
- Unpatched Vulnerabilities: Like any software, RDP can have vulnerabilities that are discovered over time. Failure to install security patches and updates can expose your system to these vulnerabilities. Cybercriminals often exploit these unpatched holes, making it crucial to keep your software current.
- Man-in-the-Middle Attacks: Attackers can intercept RDP sessions using man-in-the-middle (MitM) techniques. Attackers can capture the data exchanged during your RDP session if you use an unsecured network, such as public Wi-Fi. This risk highlights the importance of using secure connections when accessing RDP.
- Malware Infiltration: Once an attacker gains access through RDP, they can install malware on your system, potentially leading to data theft, ransomware attacks, or system corruption. Therefore, protecting your Windows PC from unauthorized access and malicious software is vital.
How to Protect Your Windows PC from RDP Risks
Taking proactive measures can significantly reduce the risks associated with RDP. Here are some essential steps for Windows end users:
Use Strong Passwords

Ensure that you set complex passwords for your RDP accounts. A strong password should include a mix of uppercase letters, lowercase letters, numbers, and special characters. Implementing multi-factor authentication (MFA) adds an extra layer of security, making it harder for attackers to gain access.
Keep Your Software Updated
Regularly update your Windows operating system and RDP software to protect against known vulnerabilities. Enable automatic updates to ensure you receive the latest security patches promptly. This practice minimizes the risk of exploitation through unpatched vulnerabilities.
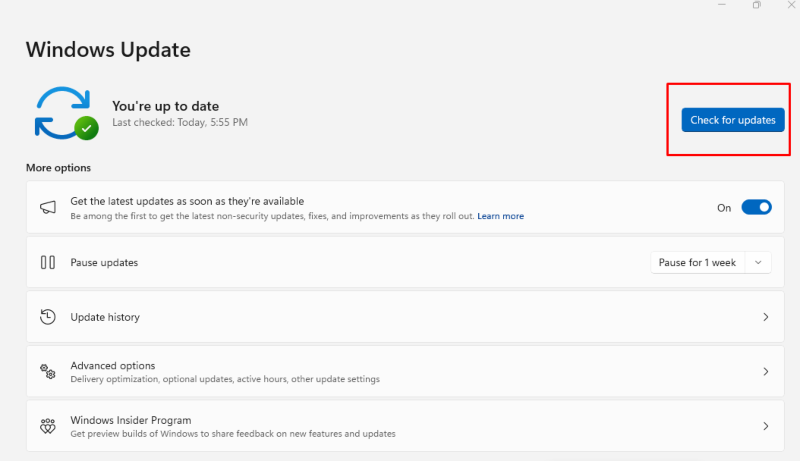
How to Check for Windows Updates:
Open Settings: Click the Start menu and select Settings (gear icon).
Access Update & Security: Click on Update & Security.
Check for Updates: Click Check for updates and install any available updates.
Restart Your PC: Follow the prompts to restart if necessary.
Enable Automatic Updates:
Access Windows Update: In Update & Security, ensure Automatic updates are enabled.
Set Active Hours: Click Change Active Hours to select your usage times.
Limit RDP Access
Restrict RDP access to specific IP addresses whenever possible. Allowing only trusted devices to connect reduces the attack surface for potential intruders. Consider using a VPN (Virtual Private Network) to create a secure tunnel for RDP connections.
Disable RDP When Not in Use
If you do not need RDP, turn it off altogether. Keeping RDP enabled increases your vulnerability to attacks, even if you believe you have robust security measures. Only enable RDP when you need to access your system remotely and turn it off afterward.
Utilize Third-Party Security Tools
Given the sophistication of today’s cyber threats, selecting a robust third-party security tool to monitor and protect your system is essential. Consider using antivirus and anti-malware solutions to detect and block malicious activities related to RDP. Tools like Fortect offer enhanced security features and monitoring capabilities to safeguard your system.
With real-time malware protection and scanning, Fortect can promptly notify you of threats and address them effectively.
Download and install Fortect now.
Conclusion
While Remote Desktop Protocol offers excellent convenience, it also comes with significant risks that can jeopardize your Windows PC’s security. Understanding these risks and implementing protective measures is essential for maintaining your system’s integrity. By following the steps outlined above, you can significantly reduce the chances of unauthorized access and secure your remote desktop connections effectively.
By focusing on these practices and staying informed about the risks, you can enjoy the benefits of RDP while minimizing potential threats to your Windows environment.




