How to Prevent Clipboard Hijacking Attacks on Windows
Clipboard hijacking is a serious security threat where malicious software or scripts intercept and modify clipboard data without your consent. Since many users copy and paste sensitive information like passwords, banking details, and personal data, clipboard hijacking can lead to financial loss and identity theft. We will explain how it works and how to prevent it on your Windows PC.
What Is Clipboard Hijacking?
It is a cyberattack where malware or malicious scripts steal or replace the data you copy. It occurs in two main ways:
- Local Clipboard Hijacking – Malware installed on your computer actively monitors and alters clipboard content.
- Web-Based Clipboard Hijacking – Malicious JavaScript embedded in websites modifies clipboard data when you copy something from the browser.
Hackers use clipboard hijacking to replace cryptocurrency wallet addresses, inject harmful URLs, or steal confidential information without detection.
How to Prevent Clipboard Hijacking on Windows
1. Use a Reliable Antivirus Program
A strong antivirus solution can detect and remove this malware before it causes harm. Ensure your security software provides real-time protection against emerging threats.
2. Keep Windows and Software Updated
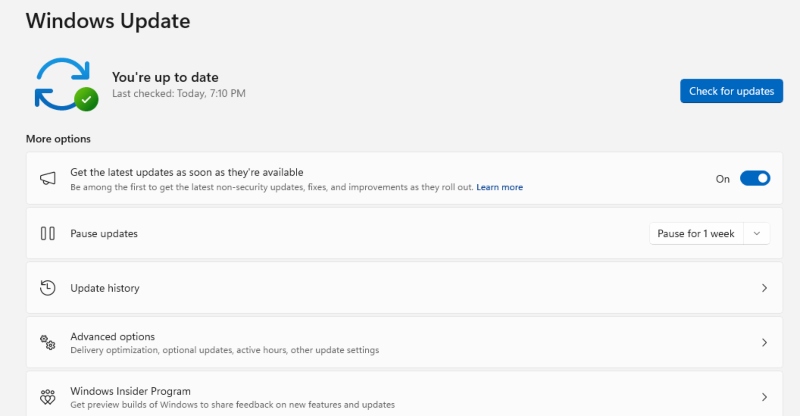
Microsoft regularly patches security vulnerabilities that hackers exploit. To prevent clipboard hijacking:
- Go to Settings > Windows Update
- Click Check for updates and install the latest security patches
- Keep browsers, applications, and security software updated
3. Disable JavaScript on Untrusted Websites
Since web-based clipboard expropriate is often executed through JavaScript, turning it off for untrusted sites can improve security.
How to Disable JavaScript in Chrome:
- Open Chrome and go to Settings
- Click Privacy and Security > Site Settings
- Scroll to JavaScript and block it for suspicious sites
4. Use Clipboard Management Software
Some clipboard managers offer enhanced security by monitoring clipboard activity and preventing unauthorized modifications. Look for software with encryption features to keep copied data safe.
5. Enable Windows Defender Exploit Protection
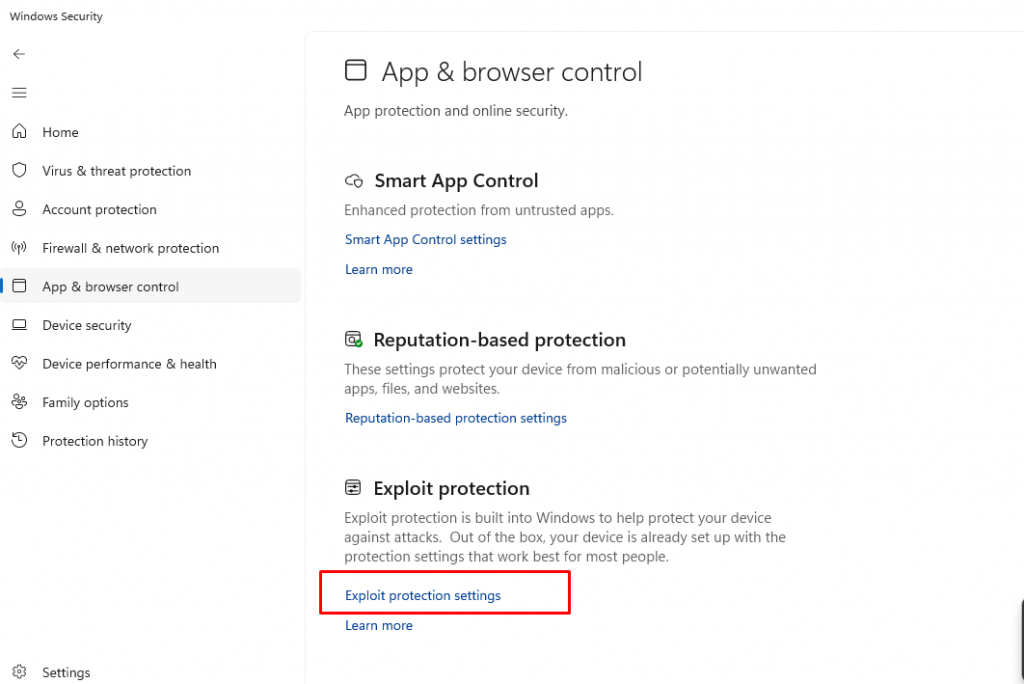
Windows has built-in security features that help protect against clipboard hijacking.
How to Enable It:
- Open Windows Security (search for it in the Start menu)
- Click App & browser control
- Select Exploit protection settings and enable clipboard protection
6. Avoid Copying Sensitive Information
Manually enter sensitive data instead of copying and pasting it, especially on websites and forms.
7. Use Browser Extensions for Clipboard Protection
Security-focused browser extensions can help detect and block clipboard hijacking attempts. Consider using NoScript or uBlock Origin to block suspicious scripts.
8. Scan Your System for Malware
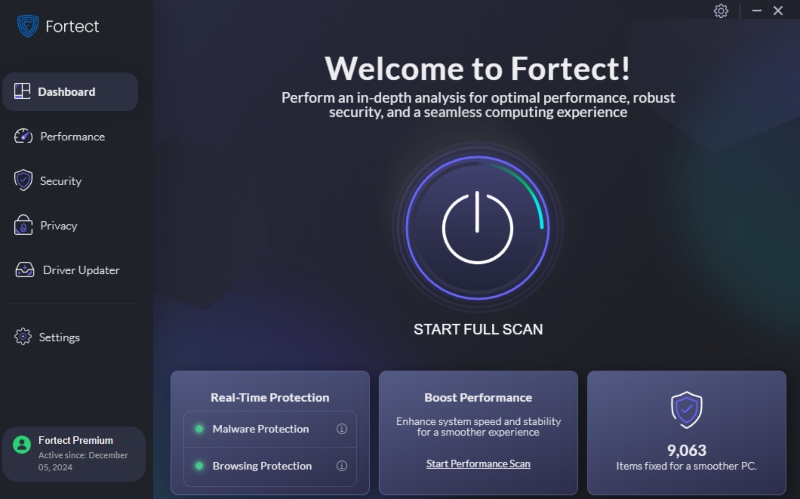
Malware infections often cause clipboard hijacking. Running a comprehensive malware scan can help identify and remove threats.
Fortect offers real-time malware protection by scanning and eliminating advanced threats, including clipboard hijackers. It automatically detects and removes malicious scripts, keeping your Windows system secure.
Download and install Fortect now.
Conclusion
Clipboard hijacking is a stealthy but dangerous attack that can compromise sensitive information. By following these preventive measures—such as using antivirus software, keeping your system updated, disabling JavaScript on untrusted sites, and utilizing clipboard management tools—you can safeguard your data against unauthorized access. Stay vigilant and practice safe browsing habits to minimize risks.




