Medusa Ransomware: Definition and Prevention for Windows Users
Medusa Ransomware is a type of malicious software designed to encrypt files on an infected system, demanding a ransom in exchange for a decryption key. This ransomware targets Windows users by exploiting security vulnerabilities, phishing emails, or malicious downloads. Once infected, victims may find their important documents, photos, and system files locked with a ransom note demanding payment in cryptocurrency.
How Medusa Ransomware Spreads
Medusa Ransomware spreads through various attack vectors, including:
- Phishing Emails – Cybercriminals send emails with malicious attachments or links.
- Exploit Kits – Vulnerabilities in outdated Windows systems are exploited.
- Trojan Downloads – Users unknowingly download malware disguised as legitimate software.
- Compromised RDP Access – Hackers gain unauthorized access through weak Remote Desktop Protocol (RDP) credentials.
Signs of a Medusa Ransomware Infection
If your Windows PC is infected with Medusa Ransomware, you may notice:
- Encrypted Files – File extensions may be changed to an unfamiliar format.
- Ransom Note – A message demanding payment appears on the desktop or within encrypted folders.
- Slow System Performance – High CPU usage due to the encryption process.
- Blocked Security Tools – Antivirus software and Windows Defender may stop working.
How to Prevent Medusa Ransomware on Windows
1. Keep Windows and Software Updated
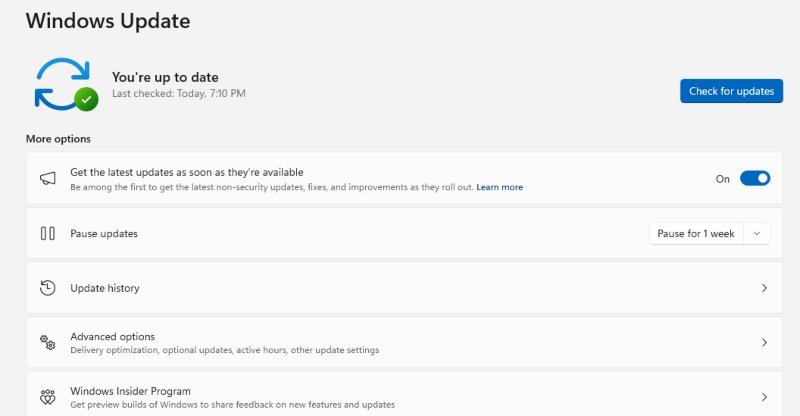
Regular Windows updates patch security vulnerabilities that ransomware exploits.
Steps to Update Windows 10:
- Click Start > Settings.
- Go to Update & Security.
- Select Windows Update > Check for updates.
- Install available updates and restart your PC if required.
2. Enable Windows Defender Ransomware Protection
Windows Defender includes a feature to prevent unauthorized file modifications.
Steps to Enable Ransomware Protection:
- Open Windows Security from the Start menu.
- Click Virus & Threat Protection.
- Scroll to Ransomware protection and click Manage ransomware protection.
- Toggle Controlled folder access to On.
3. Restrict User Privileges
Minimizing administrative access can prevent ransomware from executing system-wide changes.
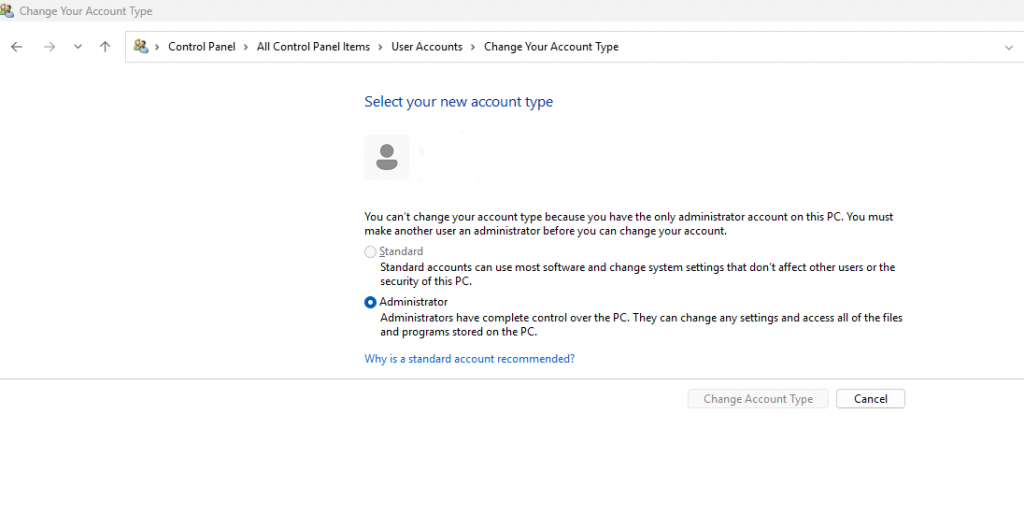
Steps to Restrict User Access:
- Open Control Panel > User Accounts.
- Select Manage another account.
- Click on the user account and choose Change the account type.
- Set the account to Standard User instead of Administrator.
4. Use Strong Passwords and Enable Multi-Factor Authentication (MFA)
Protect RDP access by:
- Creating strong, unique passwords.
- Enabling MFA for additional security.
- Disabling RDP if not needed (Control Panel > System > Remote Settings > Disable Remote Desktop).
5. Backup Important Data
Having backups ensures you don’t lose critical files to ransomware.
Steps to Set Up a Backup in Windows 10:
- Open Control Panel > Backup and Restore (Windows 7).
- Click Set up backup and select an external drive.
- Choose Let Windows choose (recommended).
- Click Next select Save settings and run backup.
How to Remove Medusa Ransomware from Windows
1. Boot into Safe Mode
- Restart your PC and press F8 before Windows loads.
- Select Safe Mode with Networking.
2. Run Windows Defender Offline Scan
- Open Windows Security.
- Go to Virus & threat protection > Scan options.
- Choose Microsoft Defender Offline scan and click Scan now.
3. Use Fortect for Ransomware Prevention and Removal
To protect your Windows PC from Medusa Ransomware, use Fortect, an all-in-one PC repair tool with real-time malware protection. Fortect not only removes ransomware infections but also proactively scans your system to detect and eliminate threats before they can cause harm. By regularly scanning your computer, Fortect helps prevent ransomware attacks, ensuring your files and system remain secure.
Download and install Fortect today not only to remove medusa malware but also to protect your computer from any types of threats.
Final Thoughts
Medusa Ransomware is a serious threat, but proactive security measures can help protect your Windows PC. Keep your system updated, restrict user access, enable security features, and back up important files regularly. If infected, act quickly to remove the ransomware and restore your data safely.




