Browser Hijacking: Removal and Prevention Tips
Browser hijacking is a common cybersecurity threat that compromises your online experience. Hijackers can change your browser settings, redirect you to unwanted websites, and expose you to harmful content. Understanding how to remove and prevent browser hijacking is crucial to maintaining a secure and smooth browsing experience.
This guide will provide essential tips on identifying, removing, and preventing browser hijacking on Windows OS and Android devices.
What is Browser Hijacking?
Browser hijacking occurs when unwanted software or malware modifies your web browser’s settings without your consent. This malicious activity is often designed to redirect your web traffic to specific websites to generate ad revenue or steal personal information.
Browser hijackers can alter your homepage, change your default search engine, and install unwanted toolbars or extensions, compromising your privacy and security.
Signs of Browser Hijackers
Recognizing the warning signs of browser hijacking can help you act quickly to protect your system and data. Here are some common indicators that your browser may have been hijacked:
- Unwanted homepage changes: Your browser’s or default search engine is changed without your permission.
- Excessive pop-ups: You see an increase in pop-up ads, even when your browser’s pop-up blocker is enabled.
- Slow browser performance: Your browser becomes slow or unresponsive, often due to added toolbars or extensions.
- Frequent redirects: Clicking on links leads you to unrelated or suspicious websites.
How to Remove Browser Hijacking
If your browser has been hijacked, it is essential to remove the unwanted software immediately and restore it to its original settings. The following methods can help you eliminate browser hijackers and protect your system.
Clear Your DNS Cache
Clearing your DNS cache can help remove any stored data that might redirect your browser to malicious websites. This process ensures that your computer communicates with the correct IP addresses and domain names.
Steps:
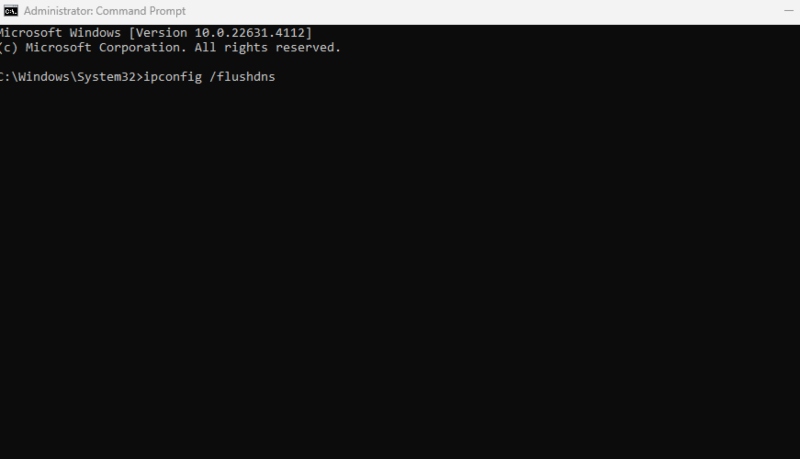
- Press Win + R to open the Run dialog box. Or type cmd in the start search bar > run as administrator
- Type cmd and press Enter to open the Command Prompt.
- Type ipconfig /flushdns and press Enter.
- You should see a confirmation message indicating that the DNS cache has been successfully flushed.
Reset Your Browser
Resetting your browser can remove unwanted extensions, toolbars, and changes to your browser’s settings. This step helps restore your browser to its default state, eliminating any modifications made by hijackers.
Steps:
- Open your browser and go to the Settings or Options menu.
- Look for Reset settings or Restore settings to their original defaults option.
- Follow the prompts to reset your browser and restart it to apply the changes.
Manually Remove the Malware
If the hijacker has installed itself as an extension or program, manually removing it can effectively stop its harmful effects. Checking your browser and computer for unknown programs can help you identify and delete malicious software.
Steps:
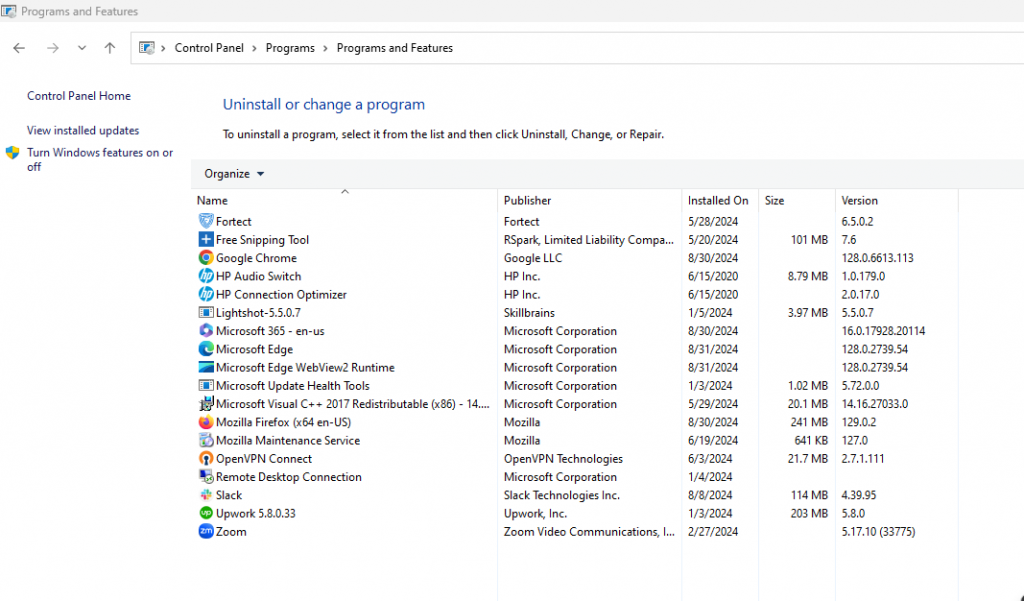
- Go to Control Panel > Programs > Programs and Features.
- Look for any suspicious or unknown programs in the list and select Uninstall.
- Open your browser, go to the Extensions or Add-ons menu, and remove unrecognized extensions.
How to Prevent Browser Hijacking
Preventing browser hijacking requires proactive steps to protect your system from malware and malicious activities. Following these best practices can safeguard your browser and personal information.
Keep Your Software Up to Date
Regularly updating your operating system, browser, and security software ensures you have the latest security patches and features. This practice reduces the risk of vulnerabilities that hijackers can exploit.
Steps:
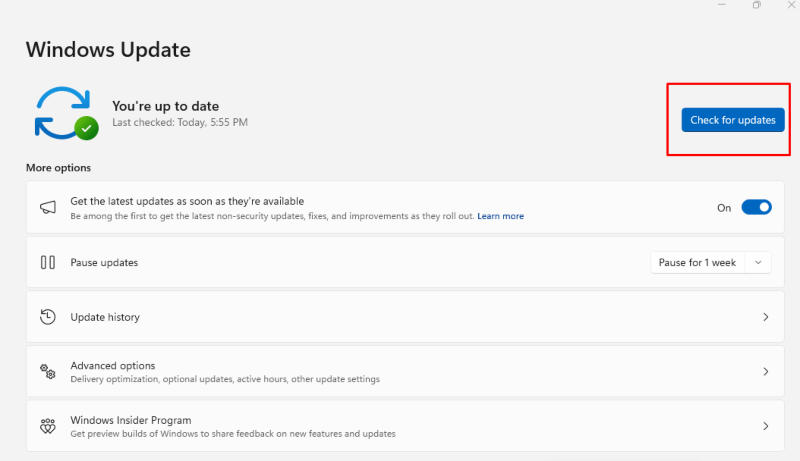
Update Your Browser:
- For most browsers, go to the browser’s menu (three dots or lines at the top-right corner for Google Chrome or Mozilla Firefox).
- Click on Help and then About [Browser Name].
- The browser will automatically check for updates and prompt you to install them if available.
Update Other Software:
- Open the Microsoft Store from the Start menu if you have apps installed from there.
- Click on Library in the lower left corner.
- Click Get Updates to check and install updates for all your Microsoft Store apps.
Avoid Suspicious Links and Attachments
Cybercriminals often use phishing emails and suspicious links to spread browser hijackers. Avoid clicking on links or downloading attachments from unknown or untrusted sources to minimize your risk.
Steps:
- Be cautious when opening emails from unknown senders.
- Hover over links to view their actual destination before clicking.
- Use a browser with built-in phishing protection to block harmful websites.
Use Caution When Downloading Software
Downloading software from untrusted sources can lead to the installation of browser hijackers and other malware. Only download software from reputable websites to ensure your system remains secure.
Steps:

- You need to verify the legitimacy of the website before downloading any software.
- Read reviews and check ratings to confirm the software’s reliability.
- Avoid downloading cracked or pirated software, as they often contain malware.
Avoid Freeware
Freeware can sometimes come bundled with unwanted software, including browser hijackers. Be selective about the free software you download, and always choose the custom installation option to deselect additional programs.
Steps:
- Choose reputable sources when downloading free software.
- Read the installation prompts carefully and opt out of any additional software.
- Regularly check your installed programs for any unexpected additions.
Secure Browser Usage
Using a secure browser and customizing its privacy settings can help prevent hijacking. Ensuring your browser has robust security features can protect your data and browsing experience.
Steps:
For Windows PC
- Always use browsers known for security features, such as Mozilla Firefox or Google Chrome.
- Adjust your browser’s privacy settings to block third-party cookies and prevent tracking.
- Install trusted security extensions to enhance your browser’s protection.
A comprehensive PC solution like Fortect is also wise for protecting your Windows PC and Android devices. Fortect’s mobile browsing protection scans for threats like browser hijacking to ensure safe browsing. It blocks intrusive push notifications, alerts you about email exposures, and prevents unauthorized changes to search settings.
The Fortect browser extension also scans websites in real time, alerting you to suspicious sites and providing detailed reports of browsing activity for better threat management.
Download and install Fortect now.
Use Antivirus Software
An effective antivirus program can provide additional protection against browser hijackers and other malware. Regularly scanning your device can detect and remove threats before they cause harm.
Steps:
- Install a comprehensive antivirus solution on your computer and mobile devices.
- Schedule regular scans to identify and remove potential threats.
- Keep your antivirus software updated to ensure it can detect the latest threats.
Conclusion
Browser hijacking is a severe threat that can disrupt online activities and compromise privacy. By understanding the signs of hijacking and knowing how to remove and prevent it, you can protect your system and personal information. Regular maintenance, cautious browsing habits, and robust security software are vital to safeguarding your browser from hijackers.
Stay vigilant and proactive to enjoy a safe and secure online experience.




