What is a Computer Worm: Prevention and Removal
If the internet is evolving, so are the threats and cybercriminals. If we fall behind, it will eventually catch us up, so as end users of Windows PCs, we need to understand how these threats, such as the computer worm, work and how we can combat them.
Unlike traditional viruses, computer worms are malware that can spread across networks without human intervention, causing significant damage. Understanding what a computer worm is, how it operates, and the steps you can take to prevent and remove it is crucial for maintaining your system’s security.
Let’s examine what a computer worm is and how it works before we proceed to removal and prevention.
What is a Computer Worm, and How Does it Work?

A computer worm is a type of malware that replicates itself to spread to other computers. Unlike viruses, worms do not need to attach themselves to existing programs or files. Instead, they exploit operating systems, software, or network vulnerabilities to spread independently.
Once inside your system, a worm can cause various issues, such as consuming bandwidth, deleting files, or opening backdoors for hackers.
Computer Worm Prevention and Removal
Understanding the best practices for preventing and removing computer worms is vital for safeguarding your devices. Below are detailed steps to help you protect your system from these malicious threats.
Removal:
Isolate the Device
When you suspect your computer is infected with a worm, the first step is to isolate the device from your network. Disconnecting from the Internet or any shared network prevents the worm from spreading to other devices.
Remove the Malware
Use a reputable antivirus or antimalware program to scan and remove the worm. Most security programs are designed to detect and eliminate worms effectively. Make sure to run a full system scan to eradicate all traces of the worm.
Prevention
Practice Safe Internet Usage

Safe browsing habits are essential for preventing computer worms. Avoid downloading files from untrusted sources, and always verify the authenticity of the websites you visit. Regularly clear your browser cache and history to minimize the risk of infection.
Be Cautious When Opening Email Attachments or Links
Worms often spread through malicious email attachments or links. Always verify the sender’s identity before opening attachments, and be wary of unexpected emails. If an email seems suspicious, it’s better to delete it than to risk opening a potentially harmful attachment.
Don’t Click on Pop-up Ads While You’re Browsing
Pop-up ads can be a source of malware, including worms. Avoid clicking on pop-up ads, especially those that seem too good to be true. Installing an ad blocker can help minimize the risk of encountering malicious ads.
Use a VPN
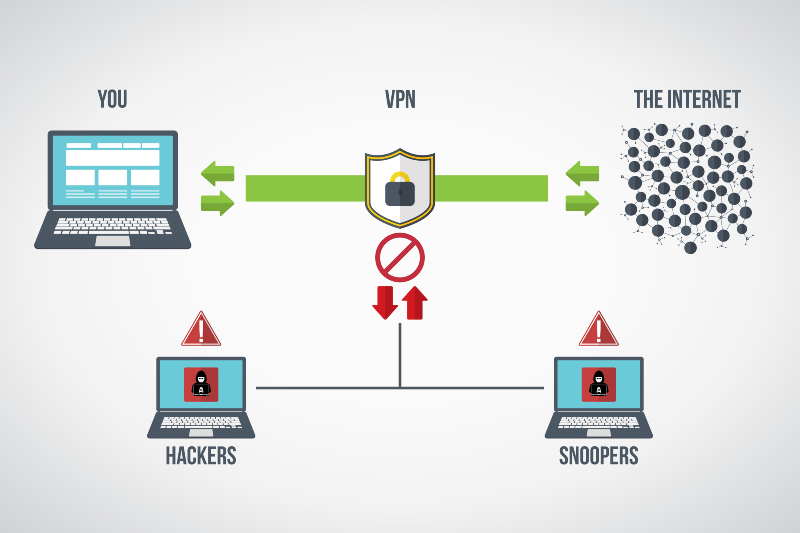
A Virtual Private Network (VPN) can provide an additional layer of security by encrypting your internet connection. This makes it more difficult for worms to exploit vulnerabilities in your network. Use a reliable VPN, especially when using public Wi-Fi.
Update Software Regularly
Outdated software can have vulnerabilities that worms exploit. Regularly updating your operating system, antivirus software, and other programs is crucial to protect your computer from new threats.
Update Passwords
Regularly updating your passwords and using complex combinations of characters can prevent unauthorized access to your system. Worms often exploit weak passwords to gain entry, so using strong, unique passwords for all accounts is essential.
Use Third-Party Automatic Updates and Malware Removal Tools
Automatic updates and third-party malware removal tools such as Fortect can add an extra layer of protection.
Fortect premium automatically scans your Windows PC for threats like computer worms, viruses, and other malware. Once done so, Fortect will notify you in real-time of issues and remove and fix the problem, boosting your Windows computer performance with real-time protection from any types of malware.
Download and install Fortect now.
Education
Educating yourself and others about computer security is one of the most effective ways to prevent worm infections. Stay informed about the latest cybersecurity threats and best practices, and share this knowledge with others in your network.
Signs Your Computer Has a Worm
- Unusual computer behavior: Slow performance, unexpected crashes, or unresponsive programs.
- Increased network activity: A sudden spike in network traffic or data usage could indicate a worm spreading to other devices.
- Unauthorized changes: New files or programs appearing without your consent.
- Frequent pop-ups: An increase in pop-up ads, even when not browsing the web.
- Disabled security software: Worms may attempt to turn off your antivirus or firewall to prevent detection.
- Low disk space: A worm can replicate itself excessively, filling up your hard drive and leaving little to no storage space.
- System slowdowns: Worms consume system resources, leading to slower performance and longer load times.
Conclusion
Computer worms are a severe threat, but you can protect your system with the proper preventive measures and timely removal actions. By understanding how worms operate and following the steps outlined in this guide, you can minimize the risk of infection and ensure your devices remain secure.
Stay vigilant, update your software, and practice safe browsing to safeguard your digital life.




