What is a Replay Attack and How to Prevent it on Windows
A replay attack is a network attack in which an attacker intercepts and retransmits valid data transmissions between a user and a service, often to gain unauthorized access or disrupt communication. For Windows users, replay attacks can lead to serious security breaches, including stolen credentials and compromised accounts.
Fortect guide explains replay attacks and provides effective prevention methods for your Windows PC.
What is a Replay Attack?
In a replay attack, a hacker captures packets of data exchanged between two parties during a legitimate communication session. These packets are then re-sent or “replayed” to the server to trick it into thinking the requests are coming from the original user. This enables the attacker to bypass authentication protocols or access secure data without decrypting or modifying the original messages.
Replay attacks can be hazardous in environments that rely on session tokens, digital signatures, or authentication credentials, as attackers can use intercepted data to mimic legitimate user behavior.
How Replay Attacks Work:
- Interception: The attacker uses packet sniffing tools to capture the communication between the user and a server.
- Re-transmission: The captured data is sent to the server, often through repeated login attempts or transaction requests.
- Exploitation: If the server doesn’t detect the malicious replays, the attacker can access user data, execute commands, or disrupt services.
How to Detect Replay Attacks
Replay attacks are often difficult to detect because they exploit legitimate data. However, sure signs may indicate that your Windows system is vulnerable or has been attacked:
- Unusual account activity: If you notice transactions or logins you didn’t authorize, it could be a sign of a replay attack.
- Multiple authentication attempts: Repeated login attempts from unknown devices or IP addresses may indicate that someone is replaying your authentication data.
- Unexplained slowdowns: An attacker may intercept or reroute your data traffic if your network or system performance is suddenly sluggish.
How to Prevent Replay Attacks on Windows
Use Encrypted Connections (TLS/SSL)
Encrypting your communication channels is the most effective way to protect against replay attacks. Transport Layer Security (TLS) and Secure Sockets Layer (SSL) encrypt data during transmission, making it harder for attackers to intercept or replay the data packets.
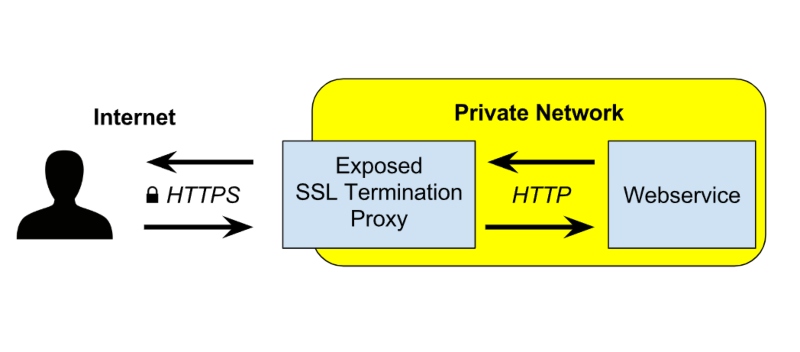
- How to ensure you’re using secure connections:
- Use websites with HTTPS encryption.
- Install and update security certificates on your Windows system.
Implement Nonce and Timestamp Mechanisms
Nonces are unique, random values generated for each session or transaction. They ensure each request is valid only once, preventing replay attacks by rejecting duplicate requests. Similarly, timestamps add a time factor to each session, allowing systems to reject requests outside of a specific timeframe.
Enable Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) significantly reduces the likelihood of successful replay attacks. Even if an attacker captures your credentials or session data, they won’t be able to bypass the additional security layers, such as verification codes sent to your phone or generated by an authentication app.

- How to enable MFA on Windows:
- For Microsoft accounts, go to Account Security Settings and enable two-step verification.
- Use third-party authentication tools like Google Authenticator or Microsoft Authenticator for extra protection.
Keep Windows and Software Updated
Replay attacks often exploit vulnerabilities in outdated software or operating systems. Regularly updating your Windows OS and installed programs ensures you’re protected with the latest security patches.
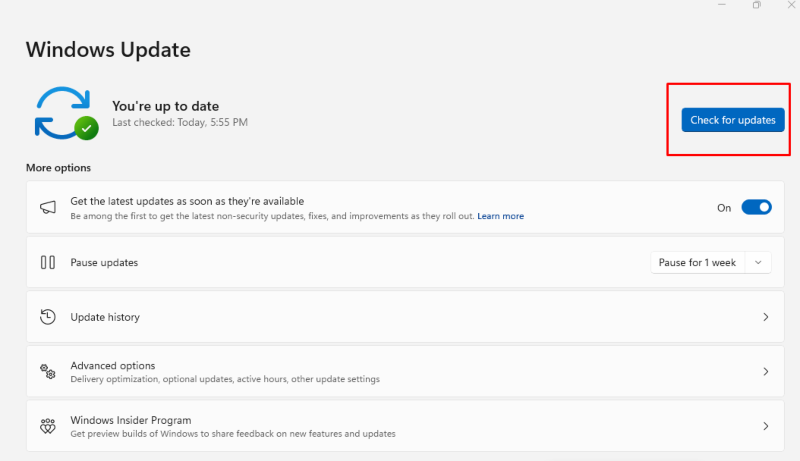
- To update Windows:
- Go to Settings > Update & Security > Windows Update.
- Enable automatic updates to ensure your system is always up-to-date.
Use Secure Wi-Fi Networks
Public and unsecured Wi-Fi networks are prime targets for replay attacks and offer little protection against packet sniffing. Always connect to trusted, secure Wi-Fi networks, and consider using a VPN (Virtual Private Network) to encrypt your data when you’re on the go.
- To set up a VPN on Windows:
- Choose a reliable VPN provider.
- Download and install the VPN software on your Windows device.
- Connect to the VPN before accessing sensitive data or performing transactions.
Monitor Account Activity
Reviewing your account activity can help you spot unauthorized access or unusual behavior. Many online services and apps allow you to check where and when your account has been accessed, making it easier to detect potential replay attacks.
- To monitor activity on Windows:
- Use the Event Viewer to review security logs and identify unusual login attempts.
- For online accounts, check the activity history under account security settings.
Or better yet, invest in a third-party solution with deep malware scanning, such as Fortect.
Consider investing in a third-party solution like Fortect for advanced malware scanning. Fortect Premium automatically scans your PC for threats and suspicious activities, including replay attacks. It provides real-time notifications and resolves issues, preventing them from recurring while optimizing and protecting your Windows PC.
Download and install Fortect now.
Conclusion
Replay attacks pose a significant threat to Windows users, but can be mitigated with proper security measures. From using encrypted connections and nonces to enabling multi-factor authentication and keeping your system updated, you can significantly reduce your risk of falling victim to a replay attack.
Always remain vigilant, especially when using public Wi-Fi or accessing sensitive data, and regularly monitor your account activity for any signs of suspicious behavior. These preventative steps will help ensure that your Windows PC remains secure and your data is protected.




